Help! All my files, images, documents have a .Moka extension. That means a ransomware virus called Moka took over your system. This page will help you to remove Moka virus from all versions of Microsoft Windows!
1. What is Moka ransomware?
SUMMARY:
| Name | Moka |
| Type | Ransomware |
| Danger Level | Very High (Ransomware viruses are of the most damaging) |
| Symptoms | PC slowness followed by files encryption and ransom demand. |
| Distribution Method | via email attachments, malicious websites, zero day exploits. |
| Detection Tool | Malware and Viruses are quite difficult to track down, since they are actively developed. Use this professional scanner to make sure you find all traces of the infection. |
Do not panic! – we will try our best to help you with this article.
Moka Ransomware is a ransomware infection that will encrypt your personal files and restricts access to data (documents, images, videos) by encrypting them with the “.Moka” extension. The authors of the malware then will ask to extort money from the victims by demanding a ransom in the form of Bitcoin cryptocurrency in exchange for access to data.
When you get infected with Moka ransomware for the first time, your computer will be scanned for images, videos and important productivity documents and files such as .doc, .docx, .xls, .pdf. When these files are detected, the ransomware encrypts them and changes their extension to “.Moka” so that they can no longer be opened.
Once the Moka ransomware has encrypted the files on your computer, the file “HOW TO RESTORE YOUR FILES.txt” will be displayed, containing the ransom note and instructions on how to contact the authors of this ransomware. Victims are invited to contact the creators of the Moka ransomware at [email protected] or [email protected].
2. How did I get infected?
Moka ransomware is spread via spam e-mails with infected attachments or by exploiting vulnerabilities in the operating system and installed programs. Here is how Moka ransomware can access your computer:
Cybercriminals send an email with false header information, which leads you to believe that it comes from a shipping company like DHL or FedEx. The email tells you that they tried to deliver you a package, but for some reason it failed. Sometimes emails claim to be notifications of a shipment made. Either way, you can’t help but be curious about what the email is about and open the attached file (or click on a link in the email). And with that, your computer is infected with Moka ransomware.
Moka ransomware has also been observed to attack victims by exploiting vulnerabilities in the program installed on the computer or the operating system itself. Commonly used programs include the operating system itself, the browser, Microsoft Office and third-party applications.
The virus appends .Moka file extension to ALL files and even renames all the files. It may also display the following message:
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-sTWdbjk1AY
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
[email protected]
Reserve e-mail address to contact us:
[email protected]
Your personal ID:
3. What should I do?
The criminals are hoping that the surprise of loosing all your files will shock you and you will pay them the ransom. However this is not a good idea, for a couple of reasons.
- Paying money to cyber criminals only encourages them to get better at their craft and extort even more people.
- You are not guaranteed in any way that your files will be decrypted successfully if you make the payment.
- There is absolutely no reason to pay until you’ve tried all the free methods first.
- Antimalware and Antivirus companies are constantly developing their products to fight the bad guys
Attention! You should be aware that all of your accounts and passwords were likely compromised. Viruses are designed to collect every piece of private information. We advise you to change all your passwords, once you clean your computer, especially if you make online banking or shopping.
The most important thing it to delete the Moka Virus, because any new files you transfer will also get encrypted and you will loose them.
4. How Can I Remove .Moka File Encryption ransomware?
SpyHunter is the recommended removal tool for the .Moka Virus File Encryption ransomware. You can use the free scanner to detect the parasite, however if you want to delete it automatically you need to register the antimalware program. What if SpyHunter failed to Detect or Remove the infection? – Find out here how to use the FREE Support.
5. Remove Moka File Encryption ransomware infection Manually
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the Ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.
- Navigate to your %appdata%/roaming folder and delete the executable.The virus temporary creates a copy of itself in the folder %appdata%
- The dropped file also changes its creation timestamp.
- This particular virus may use several files called: csrss.exe, svchost.exe, notify.exe, admin.exe, resdial.exe, ntkernl.exe, conhost.exe (however this may change as any new version will use different file names)
- Then open your Windows Registry Editor and navigate to
“Software–Microsoft–Windows–CurrentVersion–Run”
“Software–Microsoft–Windows–CurrentVersion–RunOnce”
“Software–Microsoft–Windows–CurrentVersion–Policies–Explorer”–“Run”
“Software–Microsoft–Command Processor”–“AutoRun”
Carefully review the registry entries and modify the necessary settings.
Make sure your Windows HOSTS file is clean
Some reports from users were found that the virus recently began to modify your HOST file. To fix this just do the following:
Simultaniously press the Windows Start Button and R – copy + paste the following and click OK:
notepad %windir%/system32/Drivers/etc/hosts
A new file will open. If you are hacked, there will be a bunch of other IPs connected to you at the bottom. Look at the image below:
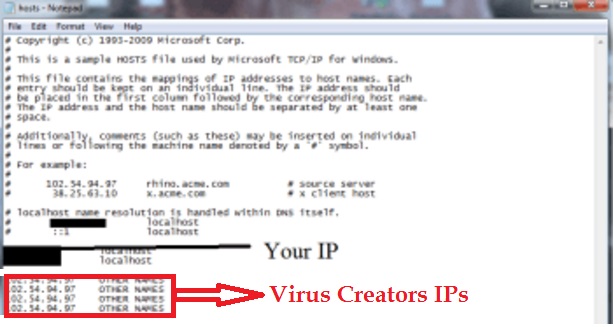
If there are suspicious foreign IPs below “Localhost” – just write to us in the comments and we will help you.
How Can I Recover .Moka files?
It is recommended first to remove the Moka Virus to prevent further damage.
- The first step to recover your lost files is a full system restore. To do this type System Restore in the windows search field and choose a restore point. Click Next until done.
- The second option is to use a software like DATA Recovery Pro program developed by Paretologic that might be able to restore some important documents.
- The third option is a program called Shadow Volume Copies. However, the recent ransomware infections delete the files necessary to fulfil the recovery process, but you can give a try.
- The fourth option is to wait some Antivirus Companies like Kaspersky or ESET to make a universal Moka files decryptor and try to decrypt the Moka files.
Nevertheless, it is highly recommended to remove the .Moka Virus File Encryption virus immediately to prevent further damage and Identity theft and hope for the best.