This page will help you to Remove Cryp1 Virus. How to Remove .Cryp1 Virus File Encryption will be described for all versions of Microsoft Windows.
Help! all my files has changed from .doc into random name .Cryp1 – as strange it may look like, this is unfortunate and means that a ransomware virus called Cryp1 Virus Files (also known as UltraCrypter) took over your system.
| Name | Cryp1 Files Virus |
| Type | Ransomware |
| Danger Level | Very High (Ransomware viruses are of the most damaging) |
| Symptoms | PC slowness followed by file encryption and ransom demand. |
| Distribution Method | via email attachments, malicious websites, zero day exploits. |
| Detection Tool | Malware and Viruses are quite difficult to track down, since they are actively developed. Use this professional .Cryp1 scanner to make sure you find all traces of the infection. |
Do not panic! – we will try our best to help you with this article. Cryp1 ransomware has an interesting development. It all started as CryptXXX and encrypted users’ files on a global scale. Kaspersky researchers made a decryptor tool and released it for free. Then CryptXXX 2.0 appeared. The improved ransomware successfully damaged many companies and home users, businesses, schools, and unfortunatelly hospitals. Kaspersky ‘s team fought back with an improved version of tool. However a new variant CryptXXX 3.0 came into being.
Cryp1 is a crypto-virus ransomware. In other words, it reproduces itself like a human virus, trying to infect more and more users; then asks for money to be paid in order to restore encrypted files. As already mentioned above, its real name is UltraCrypter. Circling the Web is the name Cryp1, which has gained more popularity. People have named it so, because of the extension it places on files – .cryp1.
UltraCrypter actually goes by many names and the most popular are:
Cryp1 Ransomware, Crypt1 Ransomware, Crypt Ransomware, UltraCrypter, UltraDeCrypter, CryptXXX 3.0 (ver. 2)
Once everything is coded you will be greeted by an html file named (Hex code ID).html, where the file name is random. The name is created out of the hexadecimal values formed by the malware in each infected computer.
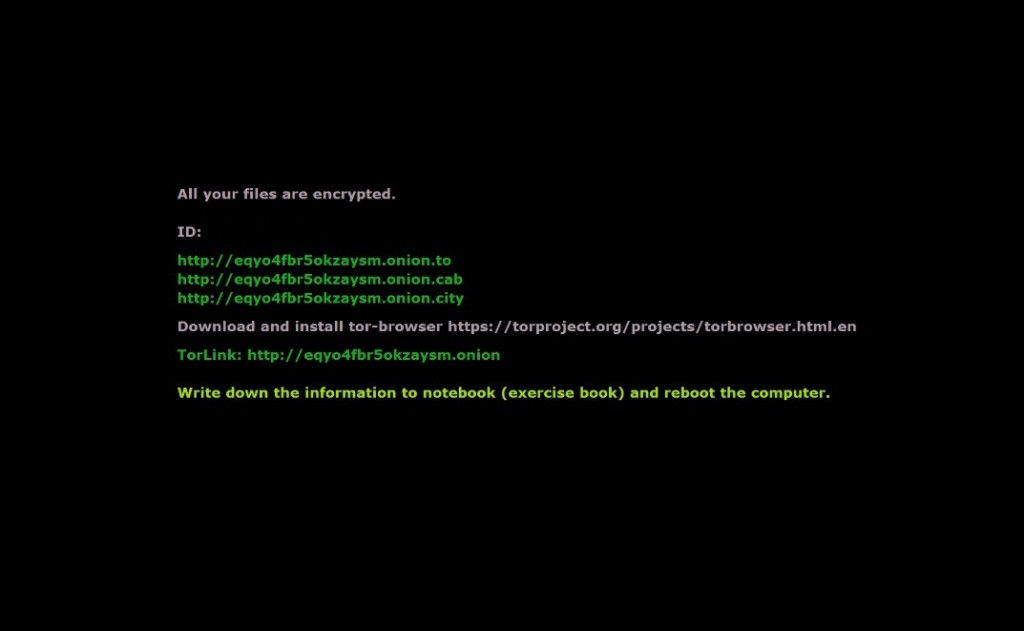
The file has different hyperlinks and a different version of the sites, which probably either redirect or the cyber criminals have bought a multitude of domains. An example of the file in question contains the following:
All your files are encrypted.
ID: [Your personal computer ID]
http://eqyo4fbr5okzaysm.onion(.)to
http://eqyo4fbr5okzaysm.onion(.)cab
http://eqyo4fbr5okzaysm.onion(.)city
Download and install tor-browser https://torproject.org/projects/torbrowser.html.en
TorLink: http://eqyo4fbr5okzaysm(.)onion
Write down the information to notebook (exercise book) and reboot the computer.
The criminals are hoping that the surprise of loosing all your files will shock you and you will pay them the ransom. However this is not a good idea, for a couple of reasons.
- Paying money to cyber criminals only encourages them to get better at their craft and extort even more people.
- You are not guaranteed in any way that your files will be decrypted successfully if you make the payment.
- There is absolutely no reason to pay until you’ve tried all the free methods first.
- Antimalware and Antivirus companies are constantly developing their products to fight the bad guys
Attention! You should be aware that all of your accounts and passwords were likely compromised. Viruses are designed to collect every piece of private information. We advise you to change all your passwords, once you clean your computer, especially if you make online banking or shopping.
How Can I Remove .Crypt1 Virus File Encryption ransomware?
Download Remover
for .Cryp1 Virus File Encryption Virus
Compatible with Microsoft Windows ![]()
SpyHunter is the recommended removal tool for the .Cryp1 Virus File Encryption ransomware. You can use the free scanner to detect the parasite, however if you want to delete it automatically you need to register the antimalware program.
What if SpyHunter failed to Detect or Remove the infection? – Find out here how to use the FREE Support.
How did I get infected?
The Cryp1 virus file encryption is currently distributed via spam emails. Once infected it will display the message:
What can I do?
The first thing it to delete the Cryp1 Virus, because any new files you transfer will also get encrypted and you will loose them. What you can actually do is recover the originals. It depends on the empty space of your HDD at the time of deletion and also how many data was written on the drive before the infection.
Cryp1 Decryptor
The Ransom note contain a link to the eqyo4fbr5okzaysm(.)onion Tor site, This is where you can access the Cryp1 Decrypter in several different languages.
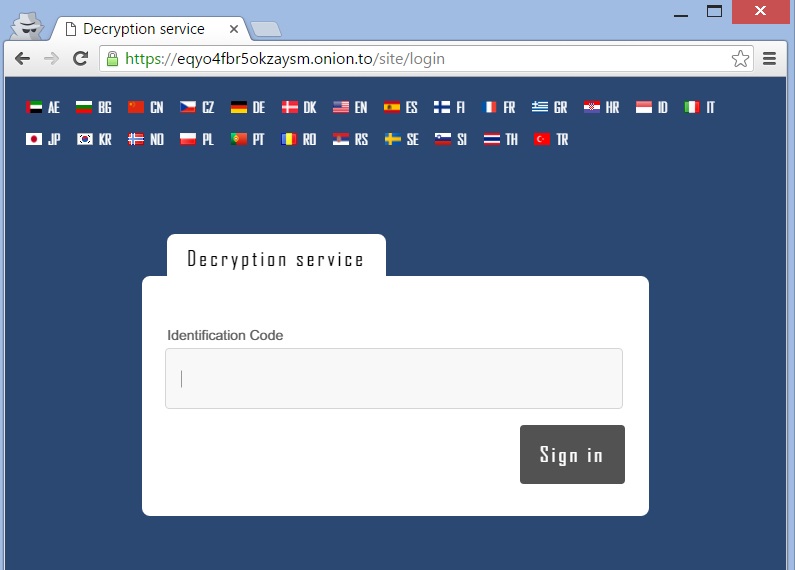
Once you choose a language, you will be prompted to enter a captcha, and then you will enter the main Cryp1 Decryptor page. This page will provide you with information on how to pay the ransom,
Remove .Cryp1 Virus File Encryption ransomware infection Manually
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the Ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.
- Navigate to your %appdata%/roaming folder and delete the executable.The virus temporary creates a copy of itself in the folder %appdata%
- The dropped file also changes its creation timestamp.
- This particular virus uses several files called: csrss.exe, notify.exe, admin.exe, resdial.exe, ntkernl.exe (however this may change as any new version will use different file names)
- Then open your Windows Registry Editor and navigate to
“Software–Microsoft–Windows–CurrentVersion–Run”
“Software–Microsoft–Windows–CurrentVersion–RunOnce”
“Software–Microsoft–Windows–CurrentVersion–Policies–Explorer”–“Run”
“Software–Microsoft–Command Processor”–“AutoRun”
Carfully revie the registry entries and modify the necessary settings.
How can I decrypt Cryp1 files?
It is reccomended first to remove the Cryp1 Virus to prevent further damage.
- The first step to recover your lost files is a full system restore. To do this type System Restore in the windows search field and choose a restore point. Click Next until done.
- The second option is to use a software like DATA Recovery Pro program developed by Paretologic that might be able to restore some important documents.
- The third option is a program called Shadow Volume Copies. However, the recent ransomware infections delete the files necessary to fulfil the recovery process, but you can give a try.
It is reccomended to remove the .Cryp1 Virus File Encryption virus to prevent further damage and wait for a free decryptor or other solution.
Bom Dia,
No dia 31/05/2016 após o almoço tive minha máquina invadida pelo Malware Ransoware, em questão de minutos ele criptografou
meus arquivos de imagens, documentos, .txt entre outros, além da extensão original do meu arquivo o Ransoware adicionou a extensão
.cryp1 e cada um deles, por exemplo o arquivo original com nome DSC0001.jpg virou DSC0001.jpg.cryp1 e portanto não tive mais acesso aos mesmos.
Após reiniciar a máquina o Ransoware adicionou um papel de parede que mostrava o caminho que deveria seguir para tentar o resgate com o ID informado.
Tentei fazer isto lá no site deles, li tudo e então enviei o arquivo de exemplo criptografado conforme instruções do site para ter certeza que eles conseguiriam descriptografar mas ainda não tive sucesso… no site do hacker só aparece a mensagem wait… onde está meu arquivo carregado…
Será que o cara não viu que enviei o arquivo? Foi ontem 06/06 às 16h e até agora 16:45h de 07/06 nada…
Bem, peço ajuda, por favor, as fotos são minha vida, estou muito triste, isto está acabando comigo.
Estou muito preocupada porque agora fiquei sem nada.
Aguardo comentários, ajudem-me por favor!